





Copyright © Expert System Solutions. All Rights reserved
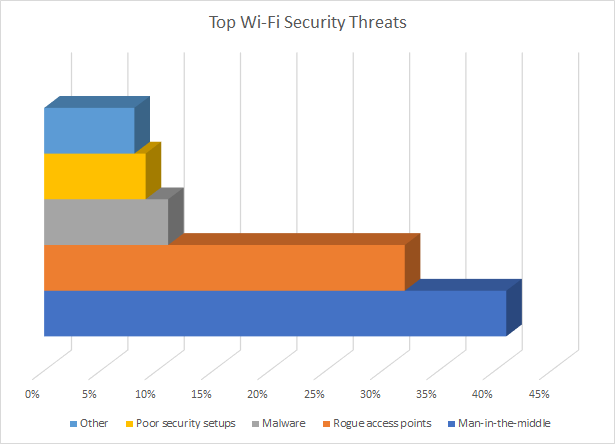
Wi-Fi networks are easy targets for hackers, even in enterprise environments. They've always been that way! According to a Data Alliance survey, man-in-the-middle attacks and rogue access points are responsible for more than 70% of the damage.
Huge Wi-Fi network vulnerability discovered

Everything started with the WEP protocol, which was really easy to crack. Then, we have gotten the improved, and yet still vulnerable WPA encryption protocol. There is an explanation for this: WPA was using a part of the old WEP architecture, which made it easier for hackers to decrypt the data packets. And today, everyone utilizes WPA2, which encrypts Wi-Fi data using the advanced AES algorithm. What could go wrong?
The WPA2 encryption mechanism may be strong, but it needs to be improved. A team of security researchers have recently published their findings concerning a very serious vulnerability which was found in the WPA2 protocol. We are writing this article because we want to help every company out there learn more about the problem, and hopefully fix it as quickly as possible. Be warned that an immediate solution may not be available for every device, though.
KRACK, the name that was given to the vulnerability, is the acronym for "key reinstallation attack". The WPA2 protocol uses a four-way handshake whenever a network client wants to join a Wi-Fi network, and then issues an encryption key that will be used by the new client to communicate with the network. By manipulating the handshake messages, an attacker may force a network client to reinstall an already existing key. As a direct consequence, TCP SYN data packets can be decrypted, so the attacker can hijack all TCP connections.
This means that the hacker will be able to inject his own malware into all the unencrypted HTTP connections. Things can get even worse if the network doesn't use the AES encryption protocol. With WPA-TKIP, a hacker will actually be able to decrypt, forge and inject data packets, causing a lot of trouble.
The WPA2 encryption mechanism may be strong, but it needs to be improved. A team of security researchers have recently published their findings concerning a very serious vulnerability which was found in the WPA2 protocol. We are writing this article because we want to help every company out there learn more about the problem, and hopefully fix it as quickly as possible. Be warned that an immediate solution may not be available for every device, though.
KRACK, the name that was given to the vulnerability, is the acronym for "key reinstallation attack". The WPA2 protocol uses a four-way handshake whenever a network client wants to join a Wi-Fi network, and then issues an encryption key that will be used by the new client to communicate with the network. By manipulating the handshake messages, an attacker may force a network client to reinstall an already existing key. As a direct consequence, TCP SYN data packets can be decrypted, so the attacker can hijack all TCP connections.
This means that the hacker will be able to inject his own malware into all the unencrypted HTTP connections. Things can get even worse if the network doesn't use the AES encryption protocol. With WPA-TKIP, a hacker will actually be able to decrypt, forge and inject data packets, causing a lot of trouble.

KRACK vulnerabilities are especially dangerous for clients running the Linux and Android operating systems. Security researchers estimate that over 40% of Android devices (smartphones, tablets, etc.) are vulnerable to this new attack.
People have learned to change their Wi-Fi passwords whenever there is a new wireless security risk. This time, changing the password will not help, though. In fact, the attacker will be able to hijack the TCP connections without even knowing the password! So, how can you protect your company from these devastating Wi-Fi-based attacks?
Begin by making sure that all the network components are running their most recent software versions. Update the server operating system. Then, patch the router and access points firmware, and install any other existing software updates for all the installed applications.
The (somewhat) good news is that this vulnerability was discovered in May 2017, when researchers have sent notifications to all the major hardware and software manufacturers. As a direct consequence, computers running Windows have been patched since October 10, 2017. Macs have been patched at the end of October, once that the High Sierra 10.13.1 macOS version was released.
Things are moving slower in the Android world, especially because so many manufacturers prefer to tweak the operating system, adapting it to their (and hopefully, their customers') needs. Google has patched its own devices at the beginning of November, but the rest of the world will have to wait more, it seems.
Since the network is one of the key assets of your company, it is important to ensure that all its components are patched. So, be sure to visit the manufacturers' websites, looking for the most recent fixes to the KRACK attack. Contact the manufacturers, asking them if they plan to release a KRACK patch anytime soon.
If you find out that a patch is not planned, it is definitely a good idea to purchase new hardware, which is already patched.
As mentioned in the introduction, the attackers are only able to intercept the TCP SYN data packets if the network clients are accessing HTTP websites. It's still quite early to draw solid conclusions, but it looks like hackers cannot access any data if the client is connected to the target website using the secure HTTPS protocol.
Fortunately, most sites use the HTTPS protocol these days, so your network should be safe as long as its users don't visit less secure websites.
People have learned to change their Wi-Fi passwords whenever there is a new wireless security risk. This time, changing the password will not help, though. In fact, the attacker will be able to hijack the TCP connections without even knowing the password! So, how can you protect your company from these devastating Wi-Fi-based attacks?
Begin by making sure that all the network components are running their most recent software versions. Update the server operating system. Then, patch the router and access points firmware, and install any other existing software updates for all the installed applications.
The (somewhat) good news is that this vulnerability was discovered in May 2017, when researchers have sent notifications to all the major hardware and software manufacturers. As a direct consequence, computers running Windows have been patched since October 10, 2017. Macs have been patched at the end of October, once that the High Sierra 10.13.1 macOS version was released.
Things are moving slower in the Android world, especially because so many manufacturers prefer to tweak the operating system, adapting it to their (and hopefully, their customers') needs. Google has patched its own devices at the beginning of November, but the rest of the world will have to wait more, it seems.
Since the network is one of the key assets of your company, it is important to ensure that all its components are patched. So, be sure to visit the manufacturers' websites, looking for the most recent fixes to the KRACK attack. Contact the manufacturers, asking them if they plan to release a KRACK patch anytime soon.
If you find out that a patch is not planned, it is definitely a good idea to purchase new hardware, which is already patched.
As mentioned in the introduction, the attackers are only able to intercept the TCP SYN data packets if the network clients are accessing HTTP websites. It's still quite early to draw solid conclusions, but it looks like hackers cannot access any data if the client is connected to the target website using the secure HTTPS protocol.
Fortunately, most sites use the HTTPS protocol these days, so your network should be safe as long as its users don't visit less secure websites.